2,49 €
Mehr erfahren.
- Herausgeber: BookRix
- Kategorie: Wissenschaft und neue Technologien
- Sprache: Englisch
Unlock the full potential of your network infrastructure with our comprehensive Cisco NX-OS Guide. Whether you're a seasoned network administrator or just diving into the world of Cisco Nexus switches, our step-by-step guide empowers you to master the art of configuring and managing Cisco NX-OS effortlessly. From essential commands and best practices to advanced features like Virtual Device Contexts (VDC), FabricPath, and Virtual Port Channels (vPC), our guide is your go-to resource for building a resilient, high-performance network. Explore in-depth tutorials, troubleshooting tips, and hands-on examples to streamline your experience with this powerful network operating system. Elevate your networking prowess with the insights and expertise found within our Cisco NX-OS Guide — your gateway to a seamlessly configured, optimized, and secure network environment.
Das E-Book können Sie in Legimi-Apps oder einer beliebigen App lesen, die das folgende Format unterstützen:
Veröffentlichungsjahr: 2023
Ähnliche
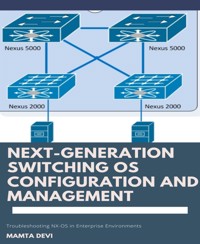
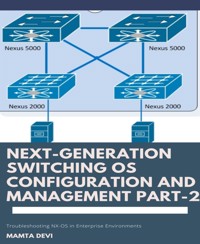
Next-Generation switching OS configuration and management Part-2
Troubleshooting NX-OS in Enterprise Environments
This eBook is based on Cisco Nexus Operating System that has been collected from different sources and people. For more information about this ebook. Kindly write to [email protected]. I will happy to help you. Copyright 2023 by Mamta Devi This eBook is a guide and serves as a next part of first guide. Previous Part Next-Generation switching OS configuration and management has already been published. This book has been written on the advice of many experts and sources who have good command over operating System, network an programming. They are listed at the end of this book. All images used in this book are taken from the LAB which is created by experts. All rights reserved, including the right to reproduce this book or portions thereof in any form whatsoever. For any query reach out to the author through email.BookRix GmbH & Co. KG81371 MunichTable of Content
We will cover below topics in this Nexus OS Security Guide.
Setting up RADIUSSetting up TACACS+Setting up SSHSetting up Cisco TrustSecSetting up IP ACLsSetting up MAC ACLsSetting up VLAN ACLsSetting up Port SecuritySetting up DHCP SnoopingSetting up Dynamic ARP InspectionSetting up IP Source GuardSetting up Keychain ManagementSetting up Traffic Storm ControlSetting up Unicast RPFSetting up Control Plane PolicingSetting up Rate LimitsConfiguring SNMPv3Security is a frequently discussed and significant concern. Cisco NX-OS Software provides comprehensive security features that safeguard NX-OS switches, protecting the network against degradation, failure, and potential data loss or compromise due to deliberate attacks. This section covers various security features, emphasizing a defence-in-depth approach to deliver a scalable, resilient, and secure data centre solution.
Setting up RADIUS in NX-OS
Authentication, Authorization, and Accounting (AAA) services facilitate identity verification, access granting, and user activity tracking on a Cisco NX-OS device. Cisco NX-OS devices support either Remote Access Dial-In User Service (RADIUS) or Terminal Access Controller Access Control device Plus (TACACS+) protocols.
Upon receiving a user ID and password combination, Cisco NX-OS devices execute local authentication or authorization using the local database or opt for remote authentication or authorization through one or more AAA servers. Security in communication between the Cisco NX-OS device and AAA servers is ensured through a preshared secret key. A common secret key can be configured for all AAA servers or specific ones.
AAA security encompasses the following services:
Authentication: This process involves verifying the identity of the person or device attempting to access the Cisco NX-OS device, based on the provided user ID and password combination. Cisco NX-OS devices support local authentication (using the local lookup database) or remote authentication (using one or more RADIUS or TACACS+ servers).
Authorization: Providing access control, AAA authorization assembles a set of attributes describing the user's authorized actions. In Cisco NX-OS software, authorization is accomplished through attributes downloaded from AAA servers. Remote servers like RADIUS and TACACS+ authorize users for specific rights by associating attribute-value (AV) pairs that define those rights.
Accounting: This service collects information, logs it locally, and sends it to the AAA server for billing, auditing, and reporting. The accounting feature maintains a log of every management session accessing the Cisco NX-OS device, which can be used for troubleshooting and auditing. The logs can be stored locally or sent to remote AAA servers.
AAA services offer advantages such as flexible and controlled access configuration, scalability, and centralized or distributed authentication methods like RADIUS and TACACS+.
A successful deployment of AAA services necessitates several prerequisites:
Verification of RADIUS or TACACS+ server reachability through IP, often conducted through a simple ping test.Configuration of the Cisco NX-OS device as a client of the AAA servers.Establishment of a secret key on both the Cisco NX-OS device and the remote AAA servers.Verification of the remote server's response to AAA requests from the Cisco NX-OS device by specifying the correct source interface.The TACACS+ protocol validates users attempting to access a Cisco NX-OS device centrally, maintaining services in a database on a TACACS+ daemon. TACACS+ offers separate authentication, authorization, and accounting facilities and uses TCP port 49 for transport communication. RADIUS, a client/server protocol, involves remote access servers communicating with a central server to authenticate users and authorize their access. RADIUS maintains user profiles centrally, ensuring a secure model for policy implementation at a single administered network point. Cisco Secure ACS 5.0 accepts authentication requests on port 1645 and port 1812, while RADIUS accounting packets are accepted on ports 1646 and 1813.
The following commands configure RADIUS authentication and accounting on a Cisco device:
Note: The provided note emphasizes that AAA configuration and operations are local to the virtual device context (VDC), except for default console methods and the AAA accounting log. AAA authentication methods for the console login apply only to the default VDC. To distribute RADIUS configuration using Cisco Fabric Services (CFS) on a Cisco NX-OS device, follow the provided instructions:
This command enables RADIUS configuration distribution through CFS. When you enable CFS distribution for a specific feature, your device becomes part of a CFS region, along with other devices in the network that have also been configured for CFS distribution for the same feature.
To apply the changes made to the RADIUS configuration in the temporary database to the running configuration and initiate the distribution of RADIUS, use the following command:
Note: It's important to be aware that RADIUS server and global keys, being unique, are not distributed through CFS sessions. Additionally, the RADIUS server group and AAA commands are not distributed via CFS.